Beyond Patching: Threat Driven Approach for Managing OT Vulnerabilities

In Homer's epic, The Odyssey, Odysseus is confronted with a perilous choice as he sails through a narrow strait guarded by two deadly threats. On one side looms Scylla, a vicious, six-headed monster ready to snatch up his sailors On the other is Charybdis, a powerful whirlpool capable of swallowing his entire ship. Both paths carry severe consequences, forcing Odysseus to carefully navigate the two evils.
Today's cybersecurity professionals face a similarly daunting dilemma when prioritizing vulnerabilities in their systems. "Charybdis" represents the whirlpool of uncertainty in applying security patches. Each patch involves downloading updates from an external entity over the Internet and introducing new, untested code into critical systems. While this process may be more straightforward for standard IT and cloud environments, industrial and operational technologies (OT) that provide critical life safety and societal services often find this approach fraught with risk. Misapplied patches can disrupt essential services with the potential for catastrophic outcomes.
In contrast, the "Scylla" facing cybersecurity teams is the relentless emergence of new vulnerabilities. Organizations are under continuous pressure to urgently patch these vulnerabilities. But with limited visibility into the actual threat each vulnerability poses, teams are forced into potentially dangerous leaps of faith.
But what if teams could clearly identify and understand the "Scylla" they face?
Illuminating the Threat
Accurate vulnerability assessment requires more than traditional scoring metrics such as CVSS. Effective defense requires deep insight into your organization's adversary intent and capabilities, which are frequently overlooked in conventional vulnerability management practices. Adversaries vary greatly in their methods and objectives. For instance, a ransomware group primarily attacking European healthcare facilities poses little threat to U.S. power grids, whereas nation-state actors targeting critical infrastructure represent significant threats.
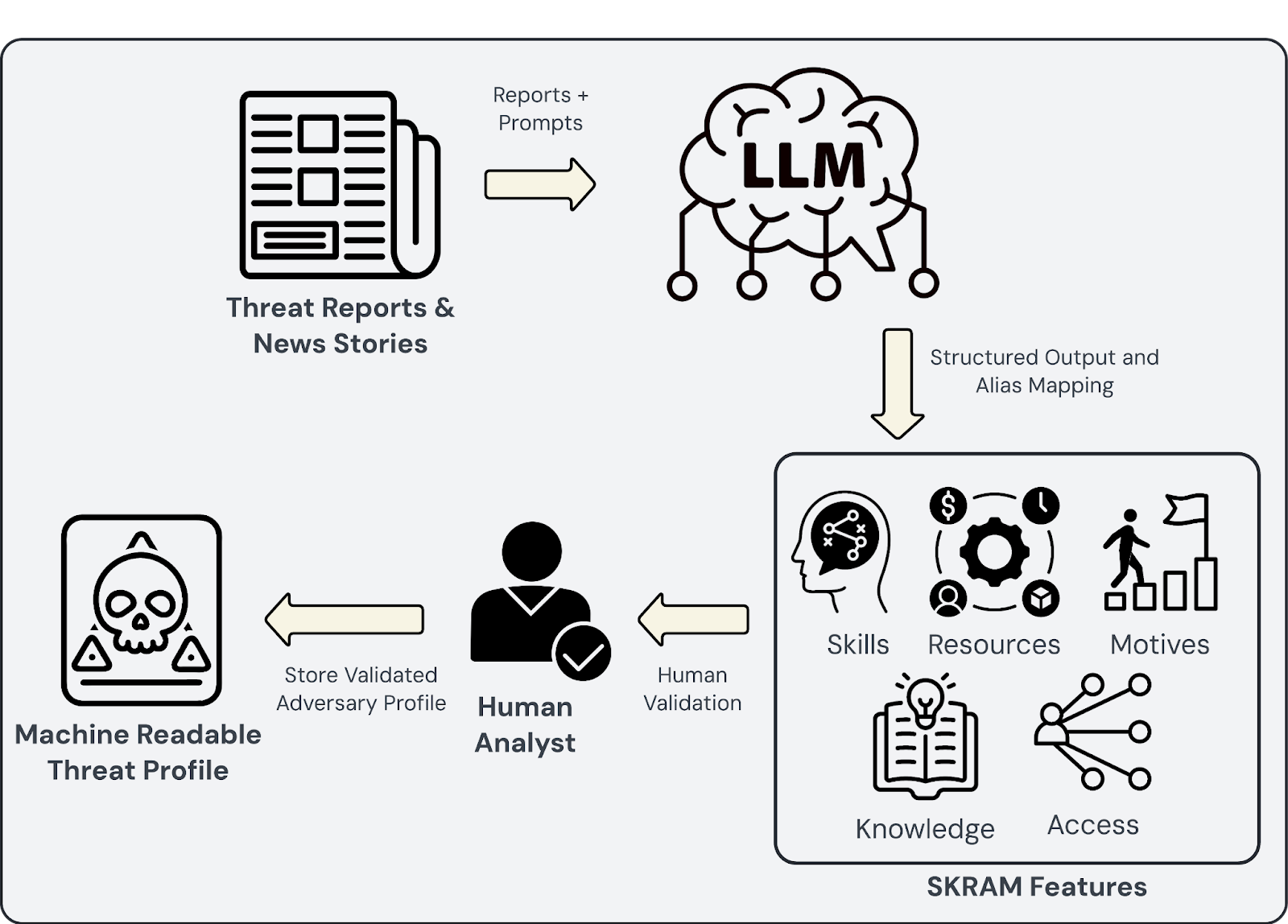
To defend effectively, cybersecurity professionals must characterize adversaries beyond static vulnerability documentation. This involves integrating dynamic threat intelligence detailing adversaries' Skills, Knowledge, Resources, Authority, and Motivation (SKRAM) into structured threat profiles. Advances in AI now enable reliable extraction and structuring of this intelligence, converting narrative reports into actionable adversary profiles compatible with structured threat intelligence frameworks like STIX.
The figure below illustrates the process of converting natural language threat reports into structured SKRAM features and STIX records:
Matching Organizations with Adversaries
Organizations rarely encounter threats randomly. Adversaries strategically select targets aligned with their objectives, capabilities, and historical victim patterns. By systematically matching structured adversary profiles with organizational characteristics such as industry sector, geographic location, and revenue, defenders can accurately identify and prioritize the specific threats most relevant to their unique risk landscape.
The Bastazo platform uses two complementary machine-learning approaches for this targeted threat assessment:
- Victim Profile Matching: This model compares organizational profiles against historical ransomware victim data, dynamically adjusting threat rankings based on real-time events.
- STIX Framework Alignment: Outside of ransomware, where victim data is not as well known, we can predict links from adversary profiles to organizations using Structured Threat Intelligence eXchange (STIX) data features such as targeted countries and sectors.
This precise threat matching empowers cybersecurity teams to strategically manage risks even when patching is impractical.
Navigating Vulnerability Remediation
Vulnerability scans frequently reveal thousands of unpatched vulnerabilities within OT networks, yet most vulnerabilities pose negligible real-world risk because adversaries cannot realistically exploit them.
Automated filtering techniques leveraging methodologies like Stakeholder Specific Vulnerability Categorization (SSVC) systematically classify vulnerabilities based on exploitability, network exposure, and potential damage. Machine-readable Common Security Advisory Framework (CSAF) advisories further assist in eliminating non-applicable vulnerabilities based on actual system configurations and providing patching alternatives. In our platform, we combine threat intelligence, SSVC, and CSAF to narrow down an organization's critical vulnerabilities then provide remediation options.
Ultimately, only a fraction of vulnerabilities emerge as genuinely critical. For these few vulnerabilities, cybersecurity teams can remediate through patching, alternative mitigations or workarounds.
Countering the Threat
Even after systematically reducing the vulnerability remediation workload, direct remediation in critical OT environments often proves infeasible due to operational constraints or safety concerns. For the remaining critical vulnerabilities, organizations can neutralize active threats through targeted countermeasures.
Contrary to the perception of cyber adversaries as obscure and unbeatable threats, precise adversary matching illuminates clear pathways for defensive actions. Detailed documentation and extensive analysis frameworks such as MITRE ATT&CK catalog adversary tactics, techniques, and mitigation strategies. Complementing ATT&CK, MITRE D3FEND provides granular mappings of defensive actions specifically designed to counter identified adversary behaviors.

These structured frameworks enable cybersecurity professionals to deploy targeted countermeasures, significantly mitigating risk in scenarios where direct remediation isn't possible. The ability to strategically leverage countermeasures ensures that critical systems remain resilient in the face of persistent cyber threats.
In our next article, we will present practical approaches for optimizing these targeted countermeasures to enable active protection for OT systems despite the challenges posed by direct remediation constraints. There is indeed a navigable route between the threats of Scylla and Charybdis that maintains both safety and reliability. Sailing through successfully requires a deeper, strategic understanding of threats posed to the system. Although the risk of modifying OT systems often pushes security teams towards inaction in their OT networks, a better understanding of the adversaries they face can unlock safe and effective remediation strategies.
For a comprehensive look at the techniques employed in threat-based remediation on the Bastazo platform, take a look at our whitepaper here.